Baidu's search for bid rankings may not be the largest industry nourished by Putian Hospital, but a lot of three areas, such as certain niche industries. Whose keywords are ranked first, his competitors are likely to employ DDoS to beat it down. This business constitutes a huge amount of traffic.
Daoge put his feet on the coffee table, which is sinister for the Leifeng Netcop River.

Daoge Wu Hanqing
This senior hacker has many identities: "The Red Book of the Arts" written by "Daoge's Blackboard News"; the head of Ali Yunyundun. In his heart, the first identity was as light as a feather, and the second as heavy as Mount Tai.
Protecting Alibaba Cloud, a 35% of China’s Web sites, is located on the cloud computing platform and the residents above it. Daoge feels that he is responsible for everything and is not to blame. Digging black production, depicting his own operational map is part of his requirement for his duties.
He told a Lei Feng network a secret: "Want to know what industries in China's black production, just look at the prohibition of Taobao sales limit is enough." DDoS attacks, extortion, dark network black market, these black industries, often will eventually involve To attack the server on Alibaba Cloud.
From his perspective, this world is full of bloody winds.
Sinister worldDDoS
We define a large traffic attack, which is generally more than 300G. In fact, according to the information we have, there are organizations in the country that can launch a T-DoS attack. Moreover, 80% of them are all played by the same organization. Most of the actual controllers of these organizations have fled abroad.
The reason for driving these attacks is very simple: money. Someone buys someone to sell. Daoge told Lei Fengwang (searching for "Lei Feng Net" public concern) that he now attacks 10G traffic and only needs a few hundred dollars.
DDoS attacks the industry, the most classic gameplay is to attack the game PW. Because the private service itself is illegal, it does not dare to appeal to the police. Black eating is a general rule of the industry. In 2013, the root domain name of the ".cn" of China's national top-level domain was once stalled. This sensation was caused by a black production attack that accidentally wounded the underlying server.
A hacking organization that controls huge bandwidth resources makes money on both sides. It collects money to attack people while extorting the attackers for higher interests. They even colluded with IDC's computer room and spent all the idle bandwidth in the computer room. The scale of business exceeded the imagination of most people.
blackmail
Unfortunately, all industries that take hot money will be spotted by hackers. P2P and Internet finance are the industries in this round of shotguns.
Because the credibility of the financial industry is very important, if the service is down, it is very likely that the trust of users will be lost, which will result in a run on the bank, which may lead to bankruptcy. It is precisely this industry that does not have strong supervision, and some involve private placement or illegal fundraising. These are excellent conditions for hacking.
Dogo talked about the two types of black play
1. Invade the P2P company's servers and steal user information. Selling these high-value customer information, advertising and black promotion from the next family.
2, threatening DDoS attacks, extortion. If the compromise is to save money, the counterparty will often come back to extortion after a while.
Finding out the purpose of hacking is crucial for defense. "According to the judgment, the next industry staring at the black production is likely to be the live broadcast industry. From the current situation, this matter has already happened." He said.
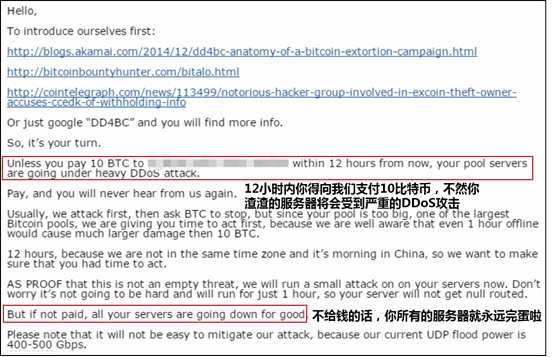
An English DDoS blackmail letter
Offensive and defensive on the cloudCloud is antidote
As a believer in cloud computing, Daoge believes that this kind of computational change that is rapidly raiding the country is, in a way, a safe cure. He gives an example:
I have visited the Cyber ​​Finance Department. Their function is to supervise various banks. On a huge screen, they can monitor each system in real time for loopholes. However, they can only see it but cannot fix it quickly. Because it corresponds to more than 1,000 business entities, their respective system models are not the same.
But if you use cloud computing as a foundation, you can unify the Iaas layer and fix the vulnerability in a short time.
In the first half of this year, Yundun repaired 460,000 loopholes for tens of thousands of customers on the cloud. This achievement made Dougge quite proud. He said that this was unimaginable in the past.
Reality cruel
Even if they rely on Alibaba Cloud, the defensive side is not dominant in the confrontation with Heihe. He said:
Unfortunately, the attacker still walks ahead. Because I can't predict the next move of the hacker.
This directly led to the security product must passively wait for the attack to take the "fire" action. For Yundun, there is still a 12-hour cycle from the hackers revealing their intent to the attack.
Black-controlled Internet attacks are like outbreaks. In most cases, infected hosts continue to spread malicious code around. In the face of a virus that spreads with "speed of light," every second is crucial.
In December 2015, cloud servers with thousands of customers were sent to the outside world. Yundun emergency handling, found that hackers are using a weak password vulnerability to spread malicious code. "Fortunately, this loophole was repaired within 12 hours. If the response time is 24 or 48 hours, it will cause greater losses." He said.
High quality standard products
If the offensive and defensive of the Internet is reduced to a map, you can see countless nodes floating on the cloud. Black production and security personnel are making every effort to compete for these nodes.
In the eyes of malicious code such as the plague spread, there are no large companies or small businesses, only servers that can be captured and servers that cannot be captured.
Almost all security companies now serve the top 3% of large customers because they have sufficient resources to hire various types of special forces. However, many SMEs that do not have a lot of security budgets are not concerned about their lives.
Daoge believes that Yundun should provide a sense of security for SMEs. In fact, there is only one inexpensive solution, that is, a software service platform (SaaS) that does not require too much labor cost, so-called high-quality standard products.
The next question then becomes: How can we make such a platform?
Data and calculationsTrain the machine as a security expert
An excellent security staff can analyze the network log to find out the clues that the server has been attacked, and unplug the enemy's stronghold from the black production attack and defense map.
But for Doug's cloud shield, it faced hundreds of thousands of cloud servers, and manual troubleshooting was not at all an option for him. How to train the machine as a security expert is the solution to the problem.
A rocket wants to go to heaven. There are two core elements: engine and fuel. Machine learning is much like a rocket. Its fuel is a huge amount of data. Its engine is a powerful computing power.
For Alibaba Cloud Cloud Shield, the daily incremental data is 300T, which is the full amount of data authorized by Alibaba Cloud's customers. The computing resources themselves are a huge advantage of Alibaba Cloud.
As a result, Yundun can perceive 80% of intrusions through pure system computing. Douglas said that this indicator is three times that of similar systems. (The technical details can be referred to another article of Lei Fengnet “Alibaba Cloud, Ye Min: Creating a “Mechanical Warriorâ€â€)

Good or bad
This detection rate is comparable to manual inspection to some extent. Doug has given a scenario:
If a customer uploads a Web shell, it may take up to a week if the security expert analyzes the full amount of data. In reality, this is often not the case. They often judge the invasion based on experience rather than a complete chain of evidence. There will be mistakes in this situation. For machines, it analyzes the full amount of data and presents a complete chain of evidence. This result is more accurate.
In terms of cost and magnitude, Yundun and labor are not comparable. Objectively speaking, what Daoge is doing, it is very difficult to repeat Aliyun.
Because cloud computing service providers are forced by policies to retain historical records for more than six months, in Yundun's big data, you can query the behavior of any IP in the past six months. Based on this, more correlation analysis can be made, such as the relationship between two attack events, which servers a black production organization is staring at, and so on.
If the security labs led by the hackers and gods are special forces, Yundun is more like a standing army to defend the basic security of Aliyun.
Dougong confidently told Lei Fengwang that there was no obvious technical difficulty before Yundun. However, given that Alibaba Cloud only has one-third of its cloud computing infrastructure resources, there are still many attacks that are out of control of Alibaba Cloud. In this case, the available data may only be the behavior of an IP. With limited data, how to use computing power becomes a key point.
Representing my great productIn fact, many people know Daoge because he likes the Blackboard.
"Daoge's Blackboard" really brought me some reputation. But I'm not a writer. What I hope is to make a good product and let the product represent me.
Daoge explains why he has abandoned the "high valuation" public number in the hacking industry. However, the hacker was not born so "pretty."
He told Lei Feng Wang about the past of Alibaba Cloud Chief Wang Jian.
At that time, everyone rumors that Dr. Wang Jian was leaving.
"Oops" is the most extensive evaluation of Alibaba Cloud's first two years. As the head of Alibaba Cloud, Wang Jian has witnessed the brothers' departments have sharpened their swords and jostleed them. After the Ali cloud is dissolved, they will divide up the troops and horses.

The original Ali cloud chief, Wang Jian, Chairman of Alibaba Group Technical Committee
Even if it is believed that cloud computing will rise in the future, but in the face of the long wait in the distant future, Daoge could not hold back and resigned. Unexpectedly, Wang Jian did not leave.
He said that he had been forced into a corner several times and he had no way back, but he really didn't go. He not only has been convinced that cloud computing has a great future, but also has been constantly investing in everything. Ma Yun did not understand cloud computing, but in the end he chose to believe in the Ph.D.
On Wang Jian’s road, the first signpost finally appeared. Aliyun used five thousand computers to connect into a huge server. This is the 5K project. This technological innovation laid the foundation for Alibaba's subsequent status as a river and lake.
"Dr. Wang Jian subverted my view of the world." Daoge said, "When he invited me to go back to Aliyun, I really felt that this matter could be achieved." This religious-like sense of mission made Dogo Do not care about his "Blackboard News", a bloody death of the cloud shield, just have all the dialogue as above.
Returning to this sense of mission itself, insist on insisting that you give up. Making a choice is simple.
Lei Feng asked: "Can this product that represents you be Ali Yunyun Shield?"
Daoge A: "I hope so."

