The old king who distributed office supplies was very happy. He received a big order today. The procurement department of an army just called him and ordered a large shipment. However, he also felt a little regret: because the troops still ordered a batch of quilts, but he does not operate quilts.
It does not matter. The army leader gave him a phone call saying that it was a merchant who had previously supplied quilts, because some things and the army were not happy. The leadership of the military hopes that Pharaoh will buy from the middle. Pharaoh dialed this phone and the other party told him that he had not done the business. However, it does not matter that a friend is doing a quilt business and let Pharaoh contact the friend.
Pharaoh made a phone call to this friend. Unexpectedly, the other party said that the goods had just been sold out. However, it does not matter. He knows a big dealer and guarantees a good price. After a round of twists and turns, Pharaoh finally contacted the big dealer by telephone and negotiated the purchase price of 50,000 pieces.
Pharaoh contacted the army leader. The military leaders felt that the price of the quilt was appropriate, but hoped that the old man would pay for the quilt on behalf of him. Finally, the military settled it with Pharaoh's money. Pharaoh once thought that since he was a friend, he could not lose his big business because of the 50,000 wounded and the feelings of the army. So readily provided for the 50,000 yuan, so that the other party directly to the military delivery.
Then, all previously contacted phones are shut down.
This is a fraud case that actually happened in Beijing. It is the tip of the iceberg of tens of thousands of fraudulent activities occurring in China every day.
In cases like this, Li Xuyang could not repeat Lei Feng for the day and night. Although Pharaoh's story has a sad ending, it is far from being the saddest. Li Xuyang’s job is to allow more than 70% of these frauds to be suspended before the victim’s final transfer, and to pull back a story from the “fault-to-die†back to “fearlessâ€.
For those victims who were rescued from the deep-seated quagmire, Li Xuyang's Tencent anti-fraud laboratory reconstructed.

Li Xuyang
All the scams in this worldIf you close your eyes and recall the various tricks you have heard or experienced, it seems that the deceptions of fraudsters are erratic and elusive. Each time it is a "new deceit" and it is hard to prevent. However, in Li Xuyang’s eyes, the first thing they have to confront is not the most sophisticated tricks. Instead, they are the “mainstream†information fraud that involves a huge amount of fraud and the most widespread fraud.
He divided these deceptions into three categories:
1, phone fraud
There are various methods for telephone fraud, but from the research data of the anti-fraud laboratory, one type actually accounts for 30%-40% of the amount involved in all types of fraud, and it has become the absolute mainstream fraud, that is, “immising the public security lawâ€. . The trick is as follows:
Before the fraudsters do such scams, they must do some preparatory work. They use overseas software to change their number to a number that is exactly the same as the public security bureau. If the change to complete agreement is too costly or technically difficult to achieve, change the form number, for example, by adding "00" before the area code.
They used the cottage number to make a phone call to the victim, telling them that there were serious criminal cases, such as money laundering and drug trafficking. If the victim denies, the fraudster will indicate that his identity information has been misappropriated by the bad guys and he has opened a criminal account in the bank. If he does not cooperate, he will be regarded as an accomplice. If the victim shows suspicion, the fraudster will take the initiative to "recommend" that he can call 114 to find out if this number is the number of the Public Security Bureau. After the victim dialed 114 and received a positive reply, he was convinced of the identity of the fraudster. At this time, another “police officer†will contact the victim and tell him that this matter is very serious. The police are fighting the criminal gang. The victim of this incident cannot tell anyone. The swindler then instructed him to transfer the “security deposit†to the security account and promised to return the case after a few days. However, the fraudsters will not close their hands. With the deep trust of the victims, the “police†will repeatedly allow him to transfer funds into “safe accounts†in the name of protecting the victims until the victim’s home breaks down.
Li Xuyang was very sad, because just before the deployment of the anti-fraud system in a certain place in early 2015, one victim had been confiscated for one month in a row, borrowing money, selling homes, and mortgages. In total, he was deceived more than 11 million yuan.
Of course, from the point of phone fraud, there are many people who have heard of posing as acquaintances, taking charge of customer service, posing as airline customer service, etc. However, the amount of fraud and harm to the victims is far less than the “public security fraudâ€. .

2. Internet fraud
The victims of cyber fraud are university students, housewives or some unemployed.
Liars will tell the victims through various channels that they can part-time job on the Internet to make money. If someone hooks, the fraudster will introduce the “profit model†in detail: part-timers only need to purchase specific goods on an e-commerce site, and then the merchant will return it to the part-timers together with the merchandise and commission. For example, if a part-time employee places a single item worth 1,000 pieces, the merchant will not actually ship the item, but will return 1,100 yuan. In order to catch long-line big fish, fraudsters designed a deep routine. They will let the part-timers buy the dozens of pieces first, and then return a few more dollars. Consciously finding the victim of a fortune, he ordered thousands of pieces of merchandise, and then there was no more.
Li Xuyang said that from the data provided by the police, the highest number of such frauds was reported, accounting for 20%-30% of the total. Fortunately, however, the amount of such fraud is generally small, from a few hundred to thousands, the highest just over 10,000.

3, "SMS +" fraud
You are on the way to the airport and suddenly you receive a text message stating that your flight was canceled for any reason. If you need a refund, you can contact customer service and attach a “customer service call†to the text message. If you call back the number, you enter the scam of the swindler. The other party will tell you that you can refund and compensate, but you must pay a certain amount of commission in advance.
Of course, you may also receive a message stating that you have won the first prize in a certain program. A notebook worth 10,000 yuan requires you to pay a certain amount of personal income in advance.
You may also receive a text message. "A bank" prompts you that online banking is about to expire. You need to log on to the website to apply for continuation. And at the end of the text message, attach the "Bank Address". The bank card and password that you enter on this page will be clearly seen by the scammers. In the twinkling of an eye, you will transfer your deposits through other channels.
Of course, some SMS scams may have been circulating for a long time. Many children's shoes are familiar. But even so, there are still countless people cheated every day. Not only that, but there are endless new tricks “coming out†every now and then.
Li Xuyang tells of a recent popular trick trick:
A car owner had a traffic accident and applied for insurance claims. As a result, a text message was suddenly received prompting the owner to settle the claim immediately. The owner was required to call back a phone number starting with “010†to receive the payment. If the owner calls back, the “insurer†will instruct him to go to the ATM next to a series of repeated operations. Eventually, he will induce the victim to adjust the ATM to the English language interface. Finally, he will transfer the fraudulent hand to the fraudster.
In the anti-fraud industry for so many years, Li Xuyang, who looked at the human world, could not help sighing: This scam is just like a screenplay. The most worrying thing is that these scripts will also be upgraded “uninterruptedâ€. Evolution never stops.

"I have traveled the furthest road, are all tricks of liar." Hope that after the children's shoes are deceived, but also have a mood so ridiculed.
To tell the truth, we have developed a classic scam and then passed the "practice" test. It takes a lot of infuriating in the "swindler community." Therefore, a "premium" scam will be constantly "polished", "improved" by the swindler groups, and even become "routine". Liars like drug addicts rely on drugs generally rely on routines.
For anti-fraud laboratories, the dependence of fraudsters on routines is their weakness. The reason is simple: once a behavior is regular, it is the time for machine recognition. The anti-fraud system can form rules that accurately determine fraud based on call length data (time data is not call content data) or network data in a large number of scams, and then telecom operators and police can monitor whether crimes occur in real time based on these rules. The fraud of fraudsters is blocked by means of text messages, telephone intervention by customer service personnel or direct intervention by the police.
Li Xuyang stated that in order to reduce the cost of confrontation with fraudsters, the details of these rules are not easily revealed. However, we can make a rough idea based on this:
A user received an overseas call, immediately dialed 114, and then talked with a strange phone for a long time. Is this model familiar? Yes, it is likely to be linked to the previously described "impersonate public security" scam. And the more you talk to this unfamiliar phone, the deeper the victim may be. You can recall your daily life carefully, and there is no normal scene that will lead you to this kind of behavior pattern. Therefore, it is clear that this rule can be used as one of the criteria for determining phone fraud.
Ashamed, it seems that anti-fraud is not difficult. Li Xuyang told Lei Feng Network that the construction of anti-fraud system is actually full of unspeakable hardships.
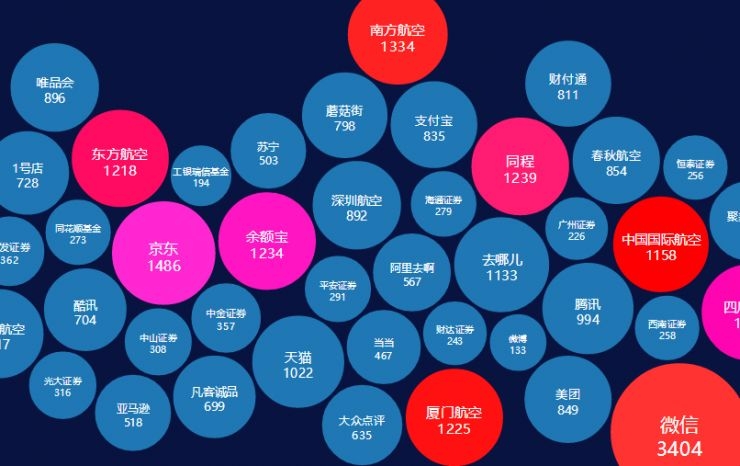
The number of counterfeiters/data from well-known Internet companies comes from Tencent
Difficult balance
"Under the same level of technology, false positives and false negatives are a side-effect. If your rules are harsh, you will raise false positives; if your rules are loose, you will increase false positives." Says, “This is a process of tuning and balancing. Only through continuous technological advancement can the two indicators of false positive rate and false negative rate fall simultaneously.â€
Taking the system of identifying public security fraud as an example, for this kind of fraud, there are several matching rules engines that jointly review. For example, just as several different experts express their opinions on the same thing, and then raise their hands to vote, if the number of experts established for the fraud reaches a certain number, the system will send out emergency reminders to operators and public security agencies. However, the drastic changes in each of these rules are based on a large amount of real fraud data. Otherwise, each system upgrade not only does not increase the accuracy of the recognition, but may also generate new missed reports and false alarms.
From 0 to 1
Liars don't sit still. They are like the most creative screenwriters and directors in the world. From time to time, they show the world their new "repertoire." There is no doubt that for these emerging routines, anti-fraud systems must have a learning process. These new fraud patterns often come from the police's case and record data.
Li Xuyang said that anti-fraud laboratories will regularly receive a large number of case details from cooperating police. After classifying by machine, the researcher will screen specific cases one by one, discover new fraud “dramaâ€, and then infer the “new trend†of the entire fraud. In the face of strong economic incentives, fraudsters are naturally motivated, continue to refine, and develop new fraudulent techniques; but as an anti-fraud security expert, it is clear that they will not receive any economic benefits from the victim. Li Xuyang and his brothers in the lab rely on their own creed of “nothing thiefâ€. This feeling is strong enough to support them from 2004 to today.
Sensitive privacy
There is one truth that speaks for itself:
"Even if it is for the purpose of anti-fraud, there is absolutely no reason to cross the boundaries of the law."
Li Xuyang said that telecom operators have full responsibility for the safety of users' communication data. Tencent has no reason, there is no way to get the specific user's call number and call duration. In other words, according to the regulations, any user's sensitive data cannot leave the operator's computer room.
This has brought a lot of difficulty to anti-fraud work. However, a "box" finally solved this problem.
We made an "Eagle Eye Box", entered our decision rule, and then handed the box over to the operator to run in their room. All data entered into the box is the data after desensitization by the operator. In other words, even if we return the box again, there is no way to decrypt the specific personal information.
Although data desensitization will have an objective impact on the accuracy of fraud, Li Xuyang believes that not touching user data is the bottom line that security personnel must comply with.

Every Internet resident has witnessed Tencent’s confrontation with swindlers and blacksmiths for more than a decade. From this point of view, there are hardly any competitors who dare to snatch Tencent's anti-fraud laboratory's title of “refining into steelâ€.
However, Tencent's decoupling from its own business and investing in increasing its research on anti-telecom fraud have caused many people to fail to understand it.
Li Xuyang told Lei Fengwang (search "Lei Feng Net" public concern) that even one of the laboratory's top-quality products "malicious website recognition engine" provides anti-fraud interfaces for many well-known organizations, and the profit is also very meager. For the anti-telephone fraud engine, it is far from profitable.
When we started doing anti-telecom fraud in 2014, none of us considered the matter of making money. We just think that this matter should be done by someone.
What impressed Li Xuyang was that when they took their anti-telecom fraud system to seek cooperation from operators, they faced very great resistance.
Operators face strict compliance requirements. For example, phone bill data (namely, call number and duration) must be within the operator and cannot come out. For many operators, anti-fraud is not their responsibility, so they are reluctant to take this risk. Many operators feel very puzzled because they do not understand what I plan to do. In their view, laboratories pay for manpower and travel, and ultimately help operators fight fraud. Operators, for various reasons, are unwilling to promote their achievements in anti-fraud.
I remember that one operator even asked me: How much money do you give us for this cooperation?
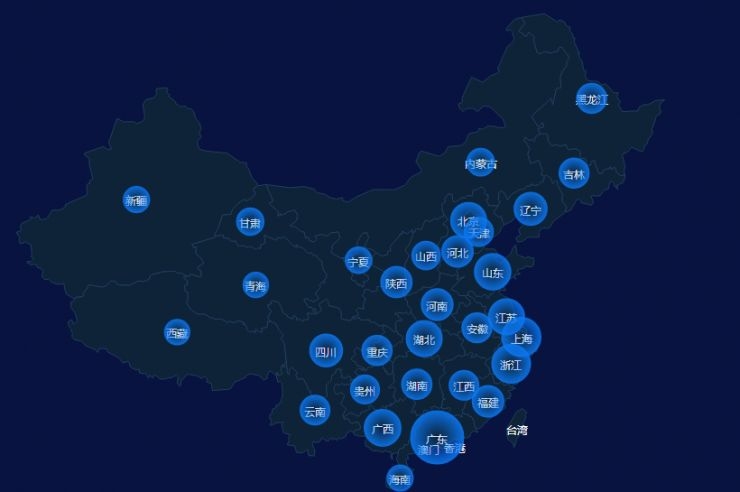
Proportion of mobile phone fraud in the country / data from Tencent
In addition to operators, Li Xuyang must also seek the support of the police. "I don't want to see that the final evaluation system is how many fraud numbers we stopped for operators. This is not result-oriented data; what we want to see is the intelligence data, is whether the amount of money involved in the fraud has fallen. And, We also need the police to provide the latest warnings - some new fraud patterns will help us upgrade our anti-fraud engine."
As you can see, in early 2015, Shenzhen Unicom became the first person to eat crabs. In the first week of the deployment of the anti-fraud system, police fraud data from Unicom users plunged 70%-80%, and has been stable so far. Li Xuyang told Lei Feng that currently, several major operators in several major provinces in China have already deployed the Hawkeye Box. As to which provinces are “gone up,†Li Xuyang strongly recommends “coding†because the news of fraudsters is very well-informed and they will tend to “fight to provinces that have not yet been protectedâ€.
Li Xuyang gave a strong suggestion that operators in wealthy provinces should deploy anti-fraud systems as soon as possible, because from the standpoint of fraudsters, a scam often requires a gang to spend a lot of time to create. For fraudsters, cheating is costly. If the fraudsters are trying their best to swindle the money they are still “not enough to payâ€, they will naturally find another way out, and maybe they will change their minds.
The anti-fraud veteran has said to Lei Fengwang more than once that if he wants to make a fortune, he must not be safe. Because the realization and commercialization of anti-fraud are very difficult, these meager profits are nothing compared to cash flow and advertising games. However, Li Xuyang and his team are on the way. For him, the biggest impetus may be the data that comes into his eyes: Without them, the amount of crimes involved in fraud each year will increase by hundreds of millions.
The word “nothing in the world†is more important to him than Taishan.
